Discovered Applications: Advanced Shadow IT Detection
The Binadox Discovered tool delivers intuitive shadow IT detection for all technical levels. Streamline unauthorized app discovery and gain complete visibility into actual SaaS usage patterns.
Uncover Hidden SaaS Applications
Simply connect your existing systems like Gmail, financial platforms, or identity providers to automatically discover unauthorized SaaS applications currently in use within your organization. The Discovered tool offers seamless integration with multiple detection methods while ensuring enterprise-grade security with comprehensive OAuth token analysis and real-time discovery notifications to maintain complete visibility across your SaaS landscape.
Gain Comprehensive Shadow IT Visibility
Once connected, the Discovered tool transforms hidden application usage into organized, actionable insights. Our platform employs multiple discovery methods including Gmail invoice scanning, financial system analysis, OAuth token inspection, and identity provider application audits. You’ll get automatic detection of unauthorized applications through invoice analysis, comprehensive OAuth token monitoring from Office 365 and Google systems, and proactive discovery notifications enabling immediate review and management of newly identified applications.
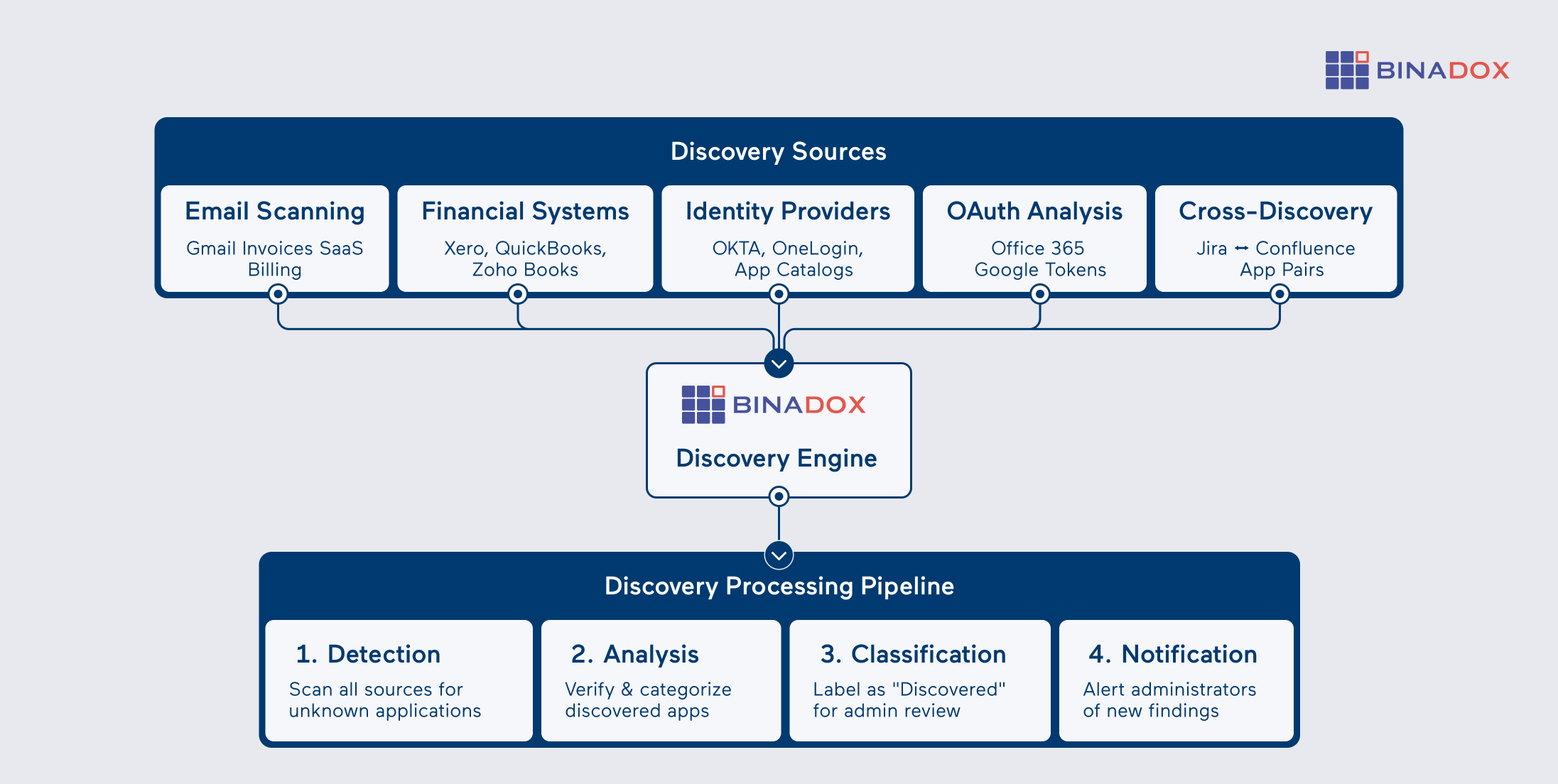
Multi-Method Discovery Engine
Our detection engine employs five distinct discovery methods to ensure comprehensive coverage. The system scans Gmail for application invoices, analyzes financial systems (Xero, QuickBooks, Zoho Books) for SaaS billing, inspects OAuth tokens from Office 365 and Google for application access patterns, reviews OKTA and OneLogin application catalogs, and identifies paired applications like Jira/Confluence that discover each other through integration patterns.
Intelligent Application Classification
Maintain organized discovery workflows with automatic application labeling and categorization. When applications are detected through any discovery method, they’re automatically flagged as “Discovered” in the system, enabling administrators to review, evaluate, and decide whether to formalize management or investigate further for security and compliance purposes.
Proactive Discovery Notifications
Stay informed about new shadow IT discoveries with intelligent notification systems. When applications are detected, the system generates immediate alerts with application details, discovery method information, and recommended next steps, enabling rapid response to potential security or cost management issues.
How It Works
Discovery Method Integration
- Email Invoice Scanning: Automated analysis of Gmail for SaaS application invoices and billing notifications
- Financial System Analysis: Direct scanning of QuickBooks, Xero, and Zoho Books for application-related expenses
- OAuth Token Inspection: Review of Office 365 and Google OAuth tokens to identify application access patterns
- Identity Provider Auditing: Analysis of OKTA and OneLogin application catalogs for pre-configured or allowed applications
- Application Cross-Discovery: Automatic detection of paired applications like Jira/Confluence through integration relationships
Discovery Processing Engine
- Instant Detection: Applications are flagged immediately upon discovery through any detection method
- Automatic Labeling: Discovered applications receive “Discovered” status for administrative review
- Parent-Child Relationships: Discovered applications remain active while their discovery source (“parent”) remains connected
- No Data Refresh Required: Discovery information is available immediately without background processing delays
Notification and Alert System
- Discovery Alerts: Immediate notifications when new applications are detected through any discovery method
- Start Saving Prompts: Action-oriented notifications encouraging formal application connection for optimization
- Discovery Unavailable Warnings: System alerts when discovery sources become unavailable or disconnected
- Administrative Notifications: Targeted alerts for administrators about newly discovered applications requiring review
Data Retention and Management
- Parent-Dependent Storage: Discovered applications remain active as long as their discovery source remains connected
- Automatic Cleanup: When discovery sources are disconnected, associated discovered applications are automatically removed
- No Independent Storage: Discovery data is tied to source connections rather than independent storage systems
- Instant Processing: Discovery information requires no background processing or data collection delays
Supported Discovery Sources
- Email Platforms: Gmail invoice scanning and application billing detection
- Financial Systems: QuickBooks, Xero, Zoho Books for comprehensive billing analysis
- Identity Providers: Office 365, G Suite, OKTA, OneLogin for OAuth and application catalog analysis
- Application Pairs: Jira/Confluence cross-discovery through integration relationships
- Manual Uploads: Invoice-based discovery through manual financial document processing
Get Complete Shadow IT Visibility with Binadox
Experience comprehensive shadow IT detection across your entire organizational infrastructure with the Discovered tool. Our multi-method platform combines intelligent scanning, OAuth analysis, and financial monitoring to deliver complete visibility into unauthorized SaaS usage without sacrificing operational efficiency.
By providing multiple discovery methods and immediate detection capabilities, the tool ensures no shadow IT applications remain hidden from administrative oversight. Your organization can join satisfied customers who have improved their security posture and cost control through systematic shadow IT discovery and management.
Whether you’re securing a small organization with focused application usage or managing enterprise environments with complex SaaS ecosystems, the Discovered tool provides the comprehensive detection and management capabilities you need to maintain complete visibility and control. Start your journey toward complete SaaS governance today and discover why organizations trust Binadox to uncover hidden applications and transform shadow IT into managed, optimized SaaS portfolios.