
Shadow IT has evolved from a minor inconvenience to a major financial and security threat for modern organizations. In today’s digital landscape, where Software as a Service (SaaS) solutions are easily accessible with just a credit card and email address, employees across all departments are independently subscribing to applications without IT department oversight. This seemingly innocent practice of unauthorized software subscriptions is creating a perfect storm of budget overruns, security vulnerabilities, and compliance nightmares that many organizations fail to fully comprehend until it’s too late.
The democratization of software procurement has fundamentally changed how businesses acquire and deploy technology solutions. While this shift has enabled rapid innovation and increased productivity, it has also introduced unprecedented challenges in SaaS spend management and control. Organizations that once maintained strict oversight over every software purchase now find themselves struggling to track hundreds of subscriptions scattered across multiple departments, payment methods, and approval processes.
Understanding the true cost of shadow IT in SaaS spending is crucial for any organization looking to maintain fiscal responsibility while enabling employee productivity. This comprehensive analysis will explore the multifaceted impact of shadow IT on organizational budgets, security posture, and operational efficiency, while providing actionable strategies to regain control over your software ecosystem.
What is Shadow IT in SaaS Context?
Shadow IT refers to the use of information technology systems, devices, software, applications, and services without explicit IT department approval or oversight. In the context of SaaS applications, shadow IT manifests as employees, teams, or departments independently purchasing and deploying cloud-based software solutions to address immediate business needs without following established procurement processes.
Unlike traditional shadow IT, which often involved physical hardware or on-premises software installations, SaaS-based shadow IT is characterized by its ease of acquisition and deployment. Modern SaaS platforms typically offer instant sign-up processes, free trial periods, and simple payment mechanisms that eliminate traditional barriers to software adoption. This accessibility has transformed shadow IT from an occasional occurrence to a widespread organizational challenge.
The SaaS distribution model has fundamentally altered the software procurement landscape. Applications can be accessed immediately through web browsers, require no installation or maintenance, and often provide immediate value to users. This convenience factor, combined with departmental budget autonomy and the pressure to maintain competitive advantages, has created an environment where shadow IT thrives.
Common examples of shadow IT in SaaS environments include marketing teams subscribing to specialized analytics platforms, sales departments adopting new CRM tools, HR teams implementing recruitment software, and development teams using project management applications. While each individual subscription may seem insignificant, the cumulative effect on organizational spending, security, and compliance can be substantial.
The Scale of the Shadow IT Problem
Recent studies reveal that the average organization uses approximately 254 SaaS applications, with IT departments typically aware of only about 30% of these subscriptions. This represents a staggering level of visibility gap that directly translates to financial and operational risks. The proliferation of cloud-based software solutions has made it easier than ever for employees to acquire and deploy applications independently, often without considering the broader organizational implications.
Gartner research indicates that shadow IT spending can account for 30-40% of total IT expenditures in large organizations. For companies with annual IT budgets of $10 million, this could represent $3-4 million in unmanaged spending annually. These figures become even more alarming when considering that SaaS subscription costs tend to increase over time through feature upgrades, user additions, and annual renewal rate increases.
The subscription model inherent to most SaaS applications contributes significantly to the shadow IT challenge. Unlike traditional software purchases that required significant upfront investment and approval processes, SaaS subscriptions often start with low monthly fees or free tiers that gradually escalate. A $15 per month subscription may seem insignificant to a department manager, but when multiplied across dozens of applications and hundreds of users, the financial impact becomes substantial.
Industry analysis shows that organizations typically discover shadow IT applications through three primary methods: security incident investigations (45%), budget audits (30%), and employee disclosure (25%). This reactive discovery approach means that most organizations are consistently operating with incomplete visibility into their software spend, making effective budget planning and security management nearly impossible.
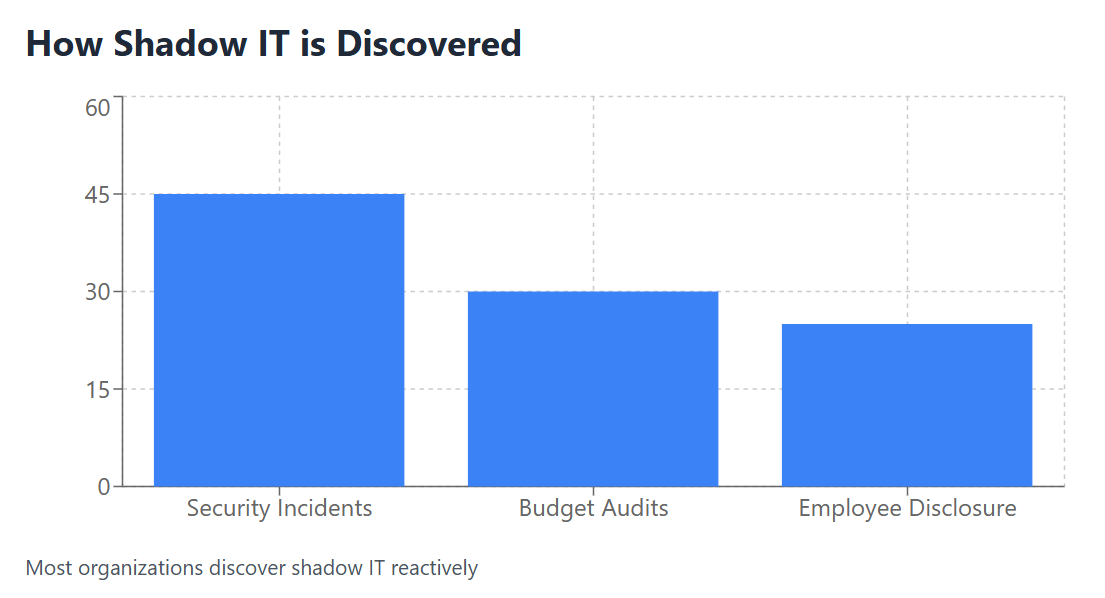
Hidden Costs of Shadow IT in SaaS Spending
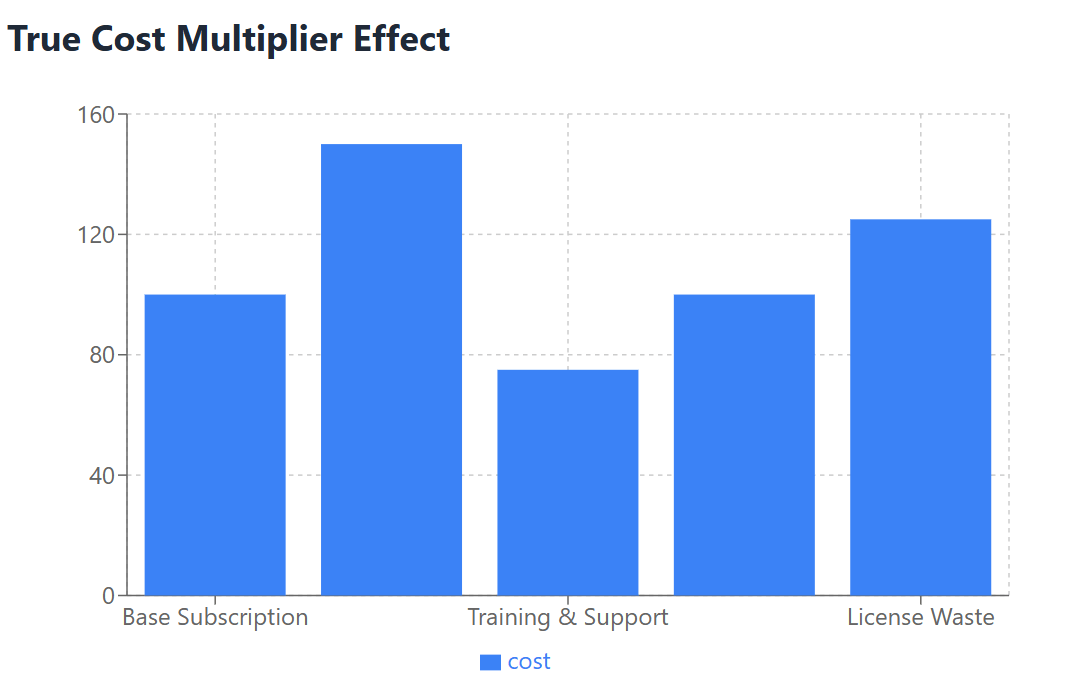
The financial impact of shadow IT extends far beyond the obvious subscription costs visible on credit card statements. Organizations face a complex web of hidden expenses that can multiply the true cost of unmanaged SaaS applications by three to five times the base subscription price.
Subscription Sprawl and Redundancy represents one of the most significant hidden costs. When departments independently select software solutions, they often choose applications with overlapping functionality, creating expensive redundancies. For example, an organization might simultaneously pay for Slack, Microsoft Teams, Google Chat, and Zoom for communication needs, when a single platform could meet all requirements. This redundancy not only wastes money but also fragments workflows and reduces overall productivity.
Integration and Data Management Costs emerge when shadow IT applications need to communicate with existing systems. Organizations often discover that their unofficial applications require expensive integration work to maintain data consistency and workflow continuity. Custom API development, data synchronization tools, and middleware solutions can cost tens of thousands of dollars per integration, far exceeding the original application subscription cost.
Compliance and Audit Expenses increase dramatically when organizations cannot maintain complete visibility into their software ecosystem. Regulatory compliance requirements, such as GDPR, HIPAA, or SOX, demand comprehensive documentation of data processing activities and vendor relationships. Shadow IT applications often lack proper documentation, forcing organizations to conduct expensive compliance audits and potentially face regulatory penalties.
Training and Support Overhead multiplies when employees use disparate tools without proper onboarding or support structures. IT departments must provide support for applications they didn’t select, evaluate, or approve, often requiring additional staff training or external consulting services. The lack of standardized training programs for shadow IT applications also reduces user efficiency and increases support ticket volumes.
License Optimization Failures occur when organizations cannot track actual usage patterns across their SaaS subscriptions. Without centralized visibility, companies often maintain expensive licenses for inactive users while simultaneously purchasing additional licenses for new employees. This inefficiency can result in 25-40% overspending on software licenses annually.
Security and Compliance Risks
Shadow IT creates significant security vulnerabilities that can expose organizations to data breaches, regulatory violations, and operational disruptions. The distributed nature of shadow IT adoption means that SaaS applications are often deployed without proper security assessments, data governance protocols, or access management controls.
Data Security and Privacy Concerns top the list of shadow IT risks. Employees frequently upload sensitive organizational data to unauthorized cloud platforms without understanding the security implications or data residency requirements. Customer information, financial records, intellectual property, and other sensitive data may be stored on servers in unknown locations, potentially violating regulatory requirements or contractual obligations.
Access Management Challenges compound when organizations cannot maintain centralized control over user authentication and authorization. Shadow IT applications often use individual employee credentials rather than single sign-on (SSO) systems, making it difficult to monitor access patterns, implement security policies, or quickly revoke access when employees leave the organization. This fragmented access management approach increases the risk of unauthorized data access and makes security incident response more complex.
Vendor Risk Assessment Gaps emerge when organizations use applications from vendors that haven’t undergone proper security evaluations. Shadow IT applications may lack adequate security certifications, data protection measures, or business continuity plans. Without proper vendor assessments, organizations risk partnering with companies that could compromise their security posture or become unavailable during critical business periods.
Regulatory Compliance Violations can result when shadow IT applications process regulated data without proper controls. Healthcare organizations using unauthorized applications to handle patient data may violate HIPAA requirements, while financial institutions could face regulatory scrutiny for inadequate data protection measures. The cost of compliance violations can range from thousands to millions of dollars in fines and remediation expenses.
Incident Response Complications multiply when security incidents involve unknown or unmanaged applications. IT security teams cannot effectively respond to threats when they lack visibility into the organization’s complete application portfolio. Shadow IT applications may not be included in security monitoring systems, backup procedures, or disaster recovery plans, creating blind spots that attackers can exploit.
Real-World Examples of Shadow IT Impact
A Fortune 500 manufacturing company discovered during a routine audit that their marketing department had independently subscribed to 47 different SaaS applications over 18 months, spending $180,000 annually on unauthorized software. Many applications provided duplicate functionality, and several contained sensitive customer data that wasn’t properly secured or backed up. The company spent an additional $300,000 on security assessments, data migration, and system consolidation to address the shadow IT proliferation.
A healthcare organization faced a $2.3 million HIPAA violation fine when investigators discovered that patient data had been uploaded to an unauthorized project management application. The shadow IT application lacked proper access controls and data encryption, resulting in the exposure of over 15,000 patient records. The organization’s legal and remediation costs exceeded $5 million, demonstrating how unauthorized software subscriptions can create devastating financial and reputational consequences.
A financial services firm discovered that their development teams were using 23 different code repository and project management tools, many of which contained proprietary algorithms and customer data. The lack of centralized SaaS governance had created a complex web of security vulnerabilities and compliance gaps. The firm invested $400,000 in security assessments and $600,000 in system consolidation to address the risks, while also implementing new policies to prevent future shadow IT adoption.
A technology startup realized during their IPO preparation that shadow IT applications represented 60% of their total software spending, with many subscriptions containing confidential product information and customer data. The due diligence process revealed significant gaps in data governance and vendor management that required extensive remediation before the public offering could proceed. The startup estimated that better SaaS spend management could have saved them $250,000 annually while reducing their regulatory and security risks.
Identifying Shadow IT in Your Organization
Detecting shadow IT requires a comprehensive approach that combines technical discovery tools, financial analysis, and organizational assessment methods. Organizations must implement systematic processes to uncover hidden SaaS applications and understand their impact on budgets, security, and operations.
Financial Analysis and Expense Tracking provides the most direct method for identifying shadow IT spending. Organizations should conduct thorough reviews of corporate credit card statements, departmental budgets, and employee expense reports to identify SaaS subscription charges. Many shadow IT applications appear as small, recurring charges that can be easily overlooked in routine financial reviews. Implementing automated expense categorization tools can help flag potential software subscriptions for further investigation.
Network Traffic Analysis offers technical insights into application usage patterns within the organization. IT departments can use network monitoring tools to identify connections to unknown cloud-based platforms and analyze data transfer patterns that might indicate unauthorized application usage. However, this method has limitations when employees use personal devices or external networks to access shadow IT applications.
Employee Surveys and Disclosure Programs encourage voluntary reporting of software usage through structured questionnaires and amnesty programs. Many employees use shadow IT applications with legitimate business justifications and are willing to disclose their usage when asked directly. Creating non-punitive disclosure environments can reveal significant portions of an organization’s shadow IT landscape while demonstrating the business value that drove the initial adoption.
Single Sign-On (SSO) Integration Gaps can reveal applications that employees access outside of approved authentication systems. Organizations with mature SSO implementations can identify potential shadow IT by analyzing authentication patterns and identifying applications that employees access without going through centralized identity management systems.
Vendor and Invoice Discovery involves systematically reviewing all vendor relationships and payment records to identify software providers that may not be officially recognized by IT departments. This approach requires collaboration between procurement, finance, and IT teams to create comprehensive visibility into organizational spending patterns.
Cloud Access Security Broker (CASB) Implementation provides ongoing monitoring capabilities for cloud application usage. CASB solutions can identify when employees access unauthorized cloud services and provide detailed analytics on application usage patterns, data transfers, and security risks associated with shadow IT applications.
Strategies to Control Shadow IT SaaS Spending
Effective shadow IT control requires balanced approaches that address immediate financial concerns while supporting employee productivity and innovation. Organizations must implement comprehensive strategies that combine policy enforcement, technology solutions, and cultural change initiatives to achieve sustainable SaaS spend management.
Centralized Software Procurement establishes clear processes for evaluating, approving, and acquiring SaaS applications while maintaining flexibility for legitimate business needs. Organizations should create streamlined approval workflows that can quickly assess and approve appropriate software requests while maintaining proper oversight and documentation. This approach requires collaboration between IT, finance, and business departments to ensure that procurement processes support rather than hinder operational efficiency.
SaaS Spend Management Tools provide centralized visibility and control over software subscriptions across the organization. Platforms like Binadox offer comprehensive monitoring capabilities that can discover existing subscriptions, track usage patterns, and identify optimization opportunities. These tools typically integrate with financial systems, cloud platforms, and identity management solutions to provide complete visibility into software spending and usage.
Budget Allocation and Departmental Accountability empower business units to make informed software decisions within approved spending limits. Organizations can allocate specific budgets for departmental software needs while implementing oversight mechanisms to ensure compliance with security and procurement policies. This approach recognizes that business departments often have legitimate needs for specialized software while maintaining organizational control over spending and risk management.
Approved Software Catalogs provide pre-vetted alternatives that meet common business needs while satisfying security and compliance requirements. IT departments can maintain curated lists of approved applications for common use cases, such as project management, communication, file sharing, and analytics. These catalogs should include detailed information about pricing, features, security capabilities, and integration options to help employees make informed decisions.
Employee Education and Awareness Programs help staff understand the risks and costs associated with unauthorized software usage while providing clear guidance on approved procurement processes. Training programs should explain the business rationale behind software policies, demonstrate how to request new applications, and highlight the security and compliance risks associated with shadow IT adoption.
Regular Audit and Discovery Processes ensure ongoing visibility into software usage patterns and spending trends. Organizations should implement quarterly or semi-annual reviews to identify new shadow IT applications, assess their business value, and determine appropriate actions such as formal approval, replacement with approved alternatives, or discontinuation.
Building Effective SaaS Governance Framework
A comprehensive SaaS governance framework provides the foundation for controlling shadow IT while enabling business innovation and productivity. Effective governance balances security and compliance requirements with operational flexibility and employee empowerment.
Policy Development and Documentation establishes clear guidelines for software acquisition, usage, and management across the organization. Governance policies should address approval processes, security requirements, data handling protocols, vendor assessment criteria, and employee responsibilities. These policies must be regularly updated to address evolving technology trends and business needs while maintaining clarity and enforceability.
Risk Assessment and Classification enables organizations to make informed decisions about software adoption based on data sensitivity, regulatory requirements, and business impact. Risk frameworks should categorize applications based on factors such as data types processed, integration requirements, vendor stability, and security capabilities. This classification system allows organizations to apply appropriate oversight levels while avoiding unnecessary bureaucracy for low-risk applications.
Vendor Management and Due Diligence ensures that SaaS providers meet organizational requirements for security, compliance, and business continuity. Due diligence processes should evaluate vendor financial stability, security certifications, data protection measures, and support capabilities. Organizations should maintain vendor scorecards and regularly reassess provider relationships to ensure ongoing compliance with organizational standards.
Data Governance and Classification addresses how sensitive information is handled within SaaS applications and establishes protocols for data protection, retention, and deletion. Data governance frameworks should specify which types of information can be stored in different categories of applications and define requirements for encryption, access controls, and backup procedures.
Integration and Architecture Standards ensure that approved applications can effectively communicate with existing systems while maintaining security and performance standards. Technical standards should address API security, data synchronization requirements, authentication protocols, and monitoring capabilities to prevent integration challenges that often drive shadow IT adoption.
Performance Monitoring and Optimization tracks the business value and cost-effectiveness of approved SaaS subscriptions to ensure that software investments deliver expected returns. Monitoring frameworks should measure application usage, user satisfaction, business outcomes, and total cost of ownership to inform future procurement decisions and identify optimization opportunities.
Technology Solutions for Shadow IT Management
Modern technology platforms provide powerful capabilities for discovering, monitoring, and managing SaaS applications across organizational environments. These solutions combine automated discovery, financial tracking, security assessment, and optimization tools to provide comprehensive shadow IT management capabilities.
SaaS Management Platforms (SMPs) offer centralized dashboards for tracking software subscriptions, usage patterns, and spending across the organization. Leading platforms like Binadox provide automated discovery capabilities that can identify SaaS applications through financial data integration, network traffic analysis, and employee surveys. These platforms typically offer features such as license optimization, renewal management, security assessments, and spending analytics.
Cloud Access Security Brokers (CASBs) provide real-time monitoring and control over cloud application access and usage. CASB solutions can identify when employees access unauthorized applications, enforce security policies, and provide detailed analytics on application usage patterns. Advanced CASB platforms offer capabilities such as data loss prevention, threat protection, and compliance monitoring specifically designed for cloud-based software solutions.
Identity and Access Management (IAM) Systems help organizations maintain centralized control over application access while providing visibility into usage patterns. Modern IAM platforms can integrate with thousands of SaaS applications to provide single sign-on capabilities, automated user provisioning, and detailed access analytics. These systems help reduce the appeal of shadow IT by making approved applications easily accessible while providing complete visibility into user activities.
Financial Management and Expense Tracking Tools integrate with corporate credit cards, procurement systems, and expense management platforms to automatically identify and categorize software subscriptions. These tools can detect recurring charges, identify duplicate subscriptions, and provide detailed analytics on software spending patterns across departments and time periods.
Integration Platforms and API Management solutions help organizations connect approved applications while maintaining security and governance standards. These platforms can reduce the appeal of shadow IT by making it easier to integrate approved applications with existing workflows and data sources. Modern integration platforms offer pre-built connectors for popular SaaS applications and provide monitoring capabilities for data flows and API usage.
Automated Compliance and Risk Assessment Tools continuously monitor SaaS applications for security vulnerabilities, compliance gaps, and policy violations. These tools can automatically assess vendor security certifications, monitor for data breaches, and alert organizations to emerging risks associated with their software portfolio.
Best Practices for SaaS Spend Control
Implementing effective SaaS spend management requires a combination of strategic planning, process optimization, and technology deployment. Organizations that successfully control software spending typically follow established best practices that balance cost management with operational efficiency and employee satisfaction.
Regular Usage Audits and License Optimization ensure that organizations pay only for software capacity they actually need. Monthly or quarterly reviews should assess user activity levels, identify inactive licenses, and right-size subscriptions based on actual usage patterns. Many organizations discover that 20-30% of their SaaS licenses are underutilized or completely unused, representing significant cost reduction opportunities.
Centralized Renewals Management prevents automatic subscription renewals for applications that no longer provide business value. Organizations should maintain comprehensive renewal calendars that provide advance notice of upcoming subscription dates and require active approval for continuation. This approach prevents the accumulation of unused subscriptions and provides regular opportunities to reassess software value and negotiate better terms.
Vendor Consolidation and Negotiation strategies focus on reducing the number of software vendors while maximizing value from preferred relationships. Organizations can often achieve significant cost savings by consolidating similar applications, negotiating enterprise agreements, and leveraging bulk purchasing power. Vendor consolidation also reduces administrative overhead and simplifies security and compliance management.
Department-Specific Spending Limits and Accountability empower business units to make software decisions within approved budgets while maintaining organizational oversight. Clear spending limits, combined with regular reporting requirements, help prevent budget overruns while enabling departmental flexibility. This approach requires robust tracking and reporting capabilities to ensure compliance with established limits.
Cost Allocation and Chargeback Models help business departments understand the true cost of their software usage and make more informed decisions about application adoption and usage. Transparent cost allocation methods can reduce unnecessary software usage while ensuring that costs are distributed fairly across the organization based on actual benefits received.
Regular Market Analysis and Alternative Evaluation ensures that organizations continue to receive competitive value from their SaaS investments. Annual or semi-annual assessments should compare current applications with emerging alternatives, evaluate pricing changes, and identify opportunities for consolidation or replacement. Market analysis should consider both financial and functional factors to ensure that software decisions support business objectives.
The Future of Shadow IT Management
The shadow IT landscape continues to evolve as new technologies, business models, and organizational structures emerge. Understanding future trends in shadow IT management is crucial for developing sustainable strategies that can adapt to changing business environments.
Artificial Intelligence and Machine Learning Integration will increasingly automate shadow IT discovery, risk assessment, and optimization processes. AI-powered platforms will be able to automatically identify unknown applications, assess their security risks, and recommend appropriate actions based on organizational policies and usage patterns. Machine learning algorithms will also improve spending optimization by predicting usage patterns and identifying consolidation opportunities.
Zero Trust Security Models will reshape how organizations approach shadow IT security management. Instead of trying to prevent all unauthorized application usage, zero trust approaches focus on securing data and access regardless of where applications are hosted or managed. This shift will enable organizations to be more flexible about application adoption while maintaining strong security controls.
Low-Code and No-Code Platform Proliferation will create new categories of shadow IT as employees build custom applications and workflows using citizen development platforms. Organizations will need to develop governance frameworks for user-created applications while providing approved alternatives that meet common business automation needs.
Edge Computing and Distributed Workforces will complicate shadow IT discovery and management as employees increasingly work from remote locations and use personal devices. Traditional network-based discovery methods will become less effective, requiring new approaches based on identity management, financial tracking, and employee disclosure.
Increased Regulatory Scrutiny will make shadow IT management a compliance imperative rather than just an operational efficiency concern. New regulations around data privacy, vendor management, and software supply chain security will require organizations to maintain complete visibility into their SaaS application portfolios.
API-First Integration Strategies will reduce the appeal of shadow IT by making it easier to connect approved applications with existing workflows and data sources. Organizations that invest in robust integration capabilities will find it easier to provide approved alternatives that meet employee needs without requiring unauthorized applications.
Improve SaaS Cost Management with Binadox
Organizations struggling with shadow IT and SaaS spend management challenges can benefit significantly from comprehensive management platforms designed specifically for modern software environments. Binadox addresses the complex challenge of shadow IT by providing complete visibility into software subscriptions across multiple departments, payment methods, and approval processes.
The platform’s automated discovery capabilities can identify SaaS applications through integration with financial systems, network traffic analysis, and employee surveys, providing organizations with comprehensive visibility into their software portfolio. This discovery process often reveals 2-3 times more applications than organizations realize they’re using, highlighting the scale of the shadow IT challenge.
Binadox’s spend optimization features help organizations identify redundant subscriptions, unused licenses, and opportunities for vendor consolidation. The platform’s analytics capabilities provide detailed insights into usage patterns, cost trends, and optimization opportunities that enable data-driven decisions about software investments. Many organizations achieve 20-30% cost reductions within the first year of implementation through better visibility and optimization.
The platform’s governance and compliance features help organizations implement policies and controls that prevent future shadow IT proliferation while maintaining business flexibility. Integration with existing procurement, identity management, and financial systems ensures that approved software adoption processes are efficient and user-friendly, reducing the incentive for employees to circumvent established procedures.
Conclusion
The true cost of shadow IT in SaaS spend management extends far beyond the visible subscription charges on corporate credit cards. Organizations face a complex web of financial, security, and operational risks that can multiply the actual cost of unmanaged software by three to five times the base subscription prices. Hidden expenses include subscription redundancies, integration costs, compliance violations, security incidents, and administrative overhead that accumulate over time and can severely impact organizational budgets and operations.
However, the solution is not to completely prohibit shadow IT adoption, which often serves legitimate business needs and drives innovation. Instead, organizations must implement comprehensive governance frameworks that balance cost control with operational flexibility and employee empowerment. Effective shadow IT management requires a combination of policy development, technology deployment, process optimization, and cultural change initiatives that address both immediate financial concerns and long-term strategic objectives.
The most successful organizations in managing SaaS spending and controlling shadow IT are those that embrace transparency, provide approved alternatives, and invest in comprehensive management platforms that offer complete visibility into their software ecosystems. By implementing proactive discovery processes, centralized governance frameworks, and optimization strategies, organizations can harness the benefits of SaaS applications while minimizing the risks and costs associated with unmanaged software adoption.
As the SaaS market continues to grow and evolve, shadow IT management will become increasingly critical for organizational success. Companies that invest in comprehensive SaaS governance and spend management capabilities today will be better positioned to leverage emerging technologies, maintain regulatory compliance, and achieve sustainable cost optimization in an increasingly complex software landscape. The key is to view shadow IT not as a problem to be eliminated, but as a business reality that requires thoughtful management and strategic oversight to maximize value while minimizing risks.

